TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 74
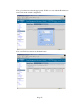
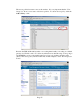
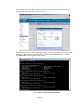
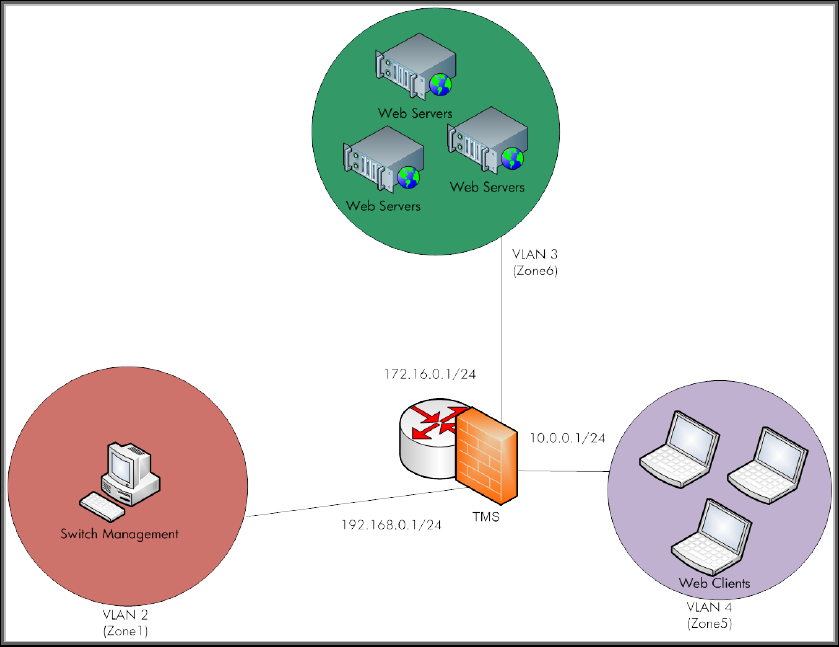
10.5 Routing Mode
10.5.1 Firewall
At the present time, we have configured the TMS zl Module with VLAN associations to
zones and IP addresses for those VLANs. However, without any specified access
policies in place, there is no traffic flowing between zones. Unlike some firewalls, the
TMS zl Module has no “priority” setting for zones with defaults allowing higher security
levels to communicate with lower security levels. With the TMS zl Module, you must
specify the access policies for any communication to take place.
Now we are ready to add some access policies. Let’s review our diagram. We are going
to have the TMS zl Module take over routing functionality from the 5406. We have
effectively done this for our simple network by assigning the TMS zl Module IP
addresses for VLANs 3 and 4. These VLANs are mapped to Zone5 for Clients and
Zone6 for Servers.
Figure 20