TMS zl Module Planning and Implementation Guide 2009-08
Table Of Contents
- Contents
- Glossary of Acronyms and Abbreviations
- 1.0 Purpose
- 2.0 Intended Audience
- 3.0 Objectives
- 4.0 Prerequisites
- 5.0 Skills
- 6.0 The HP ProCurve Threat Management Services zl Module
- 7.0 Common TMS Security Control Points
- 8.0 Deployment Considerations
- 9.0 Installation and Preparation of the TMS zl Module
- 10.0 Configuration of the TMS zl Module
- 11.0 Using multiple HP ProCurve Threat Management Services zl Modules
- Appendix A – Additional References
- Appendix B – Sample Company Information Assets Spreadsheet
- Sample “Information Assets” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Server Network Details” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “TMS Zones” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- “Firewall Rules” tab (See Embedded “Company Information Assets” Microsoft Excel 2003 spreadsheet)
- /Sample “Company Information Assets” Microsoft Excel 2003 spreadsheet
- Appendix C – Information Gathering Tools
- Appendix D - Updating Switch Software
- Appendix E – Emergency Recovery Process
Page 94
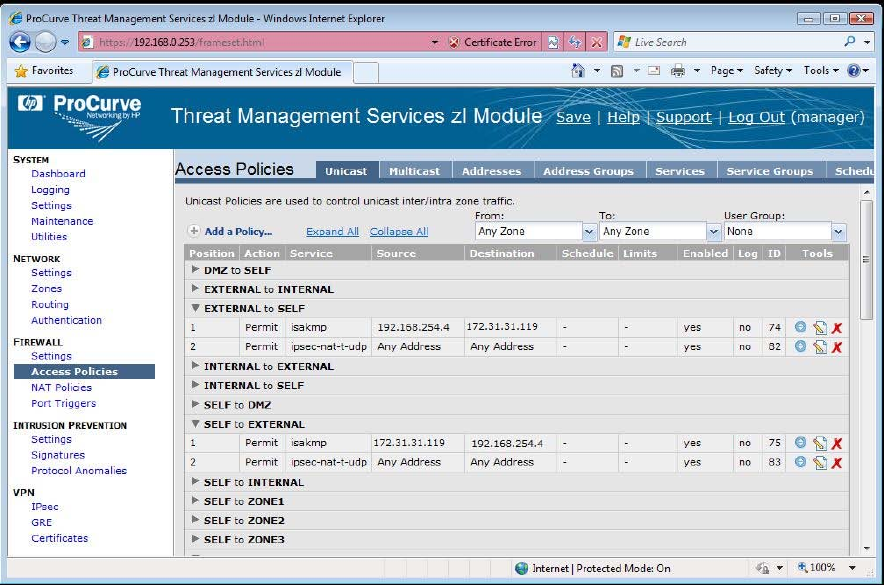
SITE B: We will need to add the ability to negotiate an IPsec session to our
access policies. We will need to allow ISAKMP to our access policies as it
performs the IPsec negotiation. We will use the IP addresses of the TMS zl
Modules as our source and destination. Also, the ISP is potentially using
NAT within the Internet Cloud, therefore, we should add a NAT traversal
access policy as well.