WESM zl Management and Configuration Guide WT.01.03 and greater
4-60
Wireless Local Area Networks (WLANs)
Configuring a WLAN
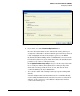
Figure 4-36. Configuring a Key for WPA/WPA2 Encryption with No Authentication
b. Enter the preshared key.
As always, you should select a key that conforms to the highest
security standards. The longer the key and the more special charac-
ters it contains, the more secure it is. (The key must be at least 22
characters to withstand a brute force attack.)
You can enter the key in one of two ways:
– Select ASCII Passphrase, and then enter a password of from 8 to 63
characters. Users must enter the same characters to access the
WLAN.
– Select 256-bit key, and then enter the key manually in hexadecimal.
Enter 16 characters in each of the four fields.
5. If you want, check the Broadcast Key Rotation box.
Because all stations must use the same broadcast key, this key is clearly
more vulnerable to hackers than the per-session keys. Periodically chang-
ing the broadcast key helps to protect your WLAN.
By default, the Wireless Edge Services zl Module does not rotate the
broadcast key. However, if you enable the feature, the default rotation
period is every 7,200 seconds (two hours).