WESM zl Management and Configuration Guide WT.01.28 and greater
4-53
Wireless Local Area Networks (WLANs)
Configuring a WLAN
Do not select the Config button to configure the WEP key; the RADIUS server
automatically generates and sends the dynamic WEP keys to successfully
authenticated users.
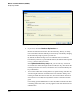
If you click the Config button, the message in Figure 4-33 is displayed. The
message does not indicate a problem: it simply informs you that you have
completed all necessary steps for configuring encryption on this WLAN.
Figure 4-33. No Need to Configure WEP Keys When the WLAN Uses 802.1X
Configuring WPA/WPA2 with 802.1X. WPA and WPA2 are similar standards,
both of which provide more robust encryption than WEP and rely on 802.1X
authentication. Both standards generate hierarchies (or sets) of encryption keys. In
the key hierarchy, each station has its own pairwise key, which the Wireless Edge
Services zl Module also knows. All stations in the same WLAN use the same group
key for multicast and broadcast traffic. WPA uses TKIP for the key hierarchy and
WPA2 uses CCMP with AES encryption.
To configure WPA/WPA2, you must select the protocol: TKIP, AES, or both. AES
is the most secure form of encryption and the one specified by WPA2 and 802.11i.
However, not all stations support AES encryption.
In the Edit screen for a WLAN, as shown in Figure 4-34, the two options for WPA/
WPA2 encryption are listed as:
■ WPA/WPA2-TKIP
■ WPA2-AES