WESM zl Management and Configuration Guide WT.01.28 and greater
5-30
Web Authentication for Mobile Users
Configuring Web-Auth
Note When you add a device’s IP address to the Allow list, that device is publicly available;
no network authentication is required to access the device. Any user can access the
device—unless that device (like the Wireless Edge Services zl Module) has its own
authentication requirements.
3. Verify that you have configured the Web pages as described in earlier sections
of this chapter.
4. Click the OK button to apply your settings and close the Web-Auth screen.
5. If you want, configure encryption for the WLAN. See “Configuring Encryption
for a Web-Auth WLAN” on page 5-30.
6. Otherwise, click the OK button on the Edit screen and the Save link at the top of
the screen.
Configuring Encryption for a Web-Auth WLAN
By itself, Web-Auth ensures that only the proper wireless users can access your
private network. However, it does not protect data transmitted over the wireless
network. For data privacy, you must enable encryption on the WLAN.
You can configure one of the following encryption options:
■ Wired Equivalent Privacy (WEP) with 64-bit keys
■ WEP with 128-bit keys
■ Wi-Fi Protected Access (WPA)/WPA2-Temporal Key Integrity Protocol (TKIP)
■ WPA2-Advanced Encryption Standard (AES)
■ both WPA/WPA2-TKIP and WPA2-AES
If you select a WEP option, the WLAN enforces static WEP. If you select a WPA
option, the WLAN enforces WPA with preshared keys (WPA-PSK). This security
takes effect before users connect to the wireless network and complete Web-Auth.
Follow these steps:
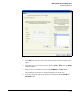
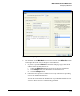
1. Access the Web-Auth WLAN’s Edit screen:
a. Select Network Setup > WLAN Setup > Configuration.
b. Select the WLAN that uses Web-Auth and click the Edit button.