WESM zl Management and Configuration Guide WT.01.28 and greater
11-22
RADIUS Server
RADIUS Authentication
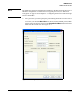
5. Configure the information that the internal RADIUS server submits to bind to
the LDAP server:
a. In the Bind DN field, enter the distinguished name for an administrator
account on the LDAP server.
For example, enter:
cn=Administrator,cn=Users,dc=mydomain,dc=com
The administrator account must be in the domain that you specify in step 5.
b. In the Bind Password field, enter the password for the name that you
specified above.
6. In the Base DN field, enter the name of the domain in which the module begins
searching for user accounts.
For example, enter:
cn=Users,dc=mydomain,dc=com
7. In the User Login Filter field, enter a filter string that searches for a user’s account
based on the username submitted during EAP.
An example of a user login filter is:
(sAMAccountName=%{Stripped-User-Name}
Another example is:
(uid=%{Stripped-User-Name:%{User-Name}})
The purpose of this filter is to verify that the LDAP server has a particular user
account—an account that matches the username that the user enters.
The syntax follows that for standard LDAP searches.
First, you enter the name of the attribute that your LDAP server uses to store a
username. This attribute might be “uid,” “sAMAccountName,” or “cd.”
Next, set the attribute equal to the username submitted through EAP. This
username is specified by one or both of the following:
• %{Stripped-User-Name}
•%{User-Name}
These strings configure the internal RADIUS server to submit the username
without appending a domain name. Make sure that the attribute you chose lists
the username in this form.