HP StorageWorks Storage Mirroring for Virtual Infrastructure user's guide (T2558-96086, February 2008)
Storage Mirroring for Virtual Infrastructure user’s guide 23
NOTE: While using Storage Mirroring for Virtual Infrastructure, you should not attempt to manually create or
delete snapshots on the protected virtual machine. Doing so will disrupt the protection of the virtual machine
and may generate unpredictable results on the source and target virtual machines.
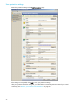
Monitor your Protected Virtual Machines
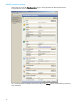
The Monitor protection page displays a status summary for each of the virtual machines you have protected
using Storage Mirroring for Virtual Infrastructure. For each protection you have configured, you can view the
current status and bytes pending.
NOTE: During the synchronization phase, the Bytes Pending column displays the un-transferred base .vmdk
file size + snapshot file size. For example, if the synchronization is 10% done, the base
.vmdk files are 5 GB,
and the snapshot files are 48 MB, the Bytes Pending value is 5 GB*90%+48 MB, which equals 4548 MB.
On this page, you can monitor and manage the protection of your protections. To manage a protection, select
a protection in the area at the top of the window, then use the buttons at the top of the page to perform the
following tasks:
•
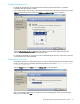
Configure Protection—Select a protection, then click the Configure Protection button to open the protection
summary for the selected protection. Click the
Change button next to setting you want to modify. For more
information about changing protection settings, see
Modify protection settings
on page 16.
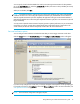
•
Delete Protection—Select a protection, then click the Delete Protection button to remove configuration
information for the selected protection.