HP Virtual Connect for c-Class BladeSystem Version 3.30 User Guide
Virtual Connect domains 45
The certificate to be uploaded must be from a certificate request sent out and signed by a Certificate Authority
for this particular Virtual Connect Manager. Otherwise, the certificate fails to match the private keys used to
generate the certificate request, and the certificate is rejected. Also, if the Virtual Connect domain has been
destroyed or re-imported, you need to repeat the steps for generating a certificate request and have it signed
by a Certificate Authority again, because the private keys are destroyed and recreated along with the Virtual
Connect domain.
If the new certificate is successfully accepted and installed by the Virtual Connect Manager, you are
automatically logged out. The HTTP server must be restarted for the new certificate to take effect.
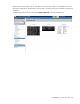
Certificates/Authentications (SSH Administration) screen
This screen lists the current user (assuming administrator privileges) of each authorized SSH key and enables
the user to add new keys. Only local users can have authorized SSH keys.
• SSH Fingerprint—Identifies the server and can be used to authenticate that the SSH client is connecting
to the correct host.
• Authorized SSH Keys—Lists the authorized SSH key data for the currently logged in user.
• Add New SSH Keys—Enables the user to create or replace the authorized SSH keys. The user can enter
the SSH keys in the text box or provide a URL to a file containing the user's SSH keys. The current content
of the Authorized SSH Keys is replaced with the new list of SSH keys after clicking Set SSH Keys. The key
file should contain the User Name of a local user at the end of the public key. Each key is associated
with a local user account.