HP ProtectTools security software 2011 - Technical white paper
you want shredded automatically, and define the schedules. This level of control is available in File
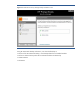
Sanitizer settings (Figure 12), where security levels can be selected as well custom control over types
of information to erase (i.e. cookies, temporary files, etc.). File Sanitizer can then be set up to erase
the predefined files based on events such as Windows shutdown.
Figure 12. HP ProtectTools File Sanitizer setup menu
File sanitization is more intensive process than simple file deletion. The amount of time it takes to
delete a file or a group of files is directly related to their size. File Sanitizer is therefore not a
replacement for simple file deletion; it is instead meant to complement it. Free Space Bleaching can
also be set up to bleach the hard drive at a predetermined schedule.
Computrace® LoJack Pro for HP ProtectTools
Computrace LoJack Pro, powered by Absolute Software (purchased separately), addresses the
growing problem of computers that are lost or stolen. Activating this software enables the Computrace
agent, which remains active in your computer even if the hard drive is reformatted or replaced. LoJack
Pro permits remote monitoring, management, and tracking of your computer. Absolute’s recovery
team will assist in your computer’s recovery if it is lost or stolen, depending on geographic location.
Privacy Manager for HP ProtectTools
Privacy Manager for HP ProtectTools allows you to secure the documents and emails you create within
Microsoft Office applications. With Privacy Manager you can be sure that only those friends, clients
or colleagues you select will be able to open and read a given document or email. Your recipients
can be certain that such files were created by you, and never modified by anyone else, since Privacy
Manager leverages the strong, multifactor user authentication provided by HP ProtectTools. The result
is that you can now take control of the information you create and communicate to ensure its privacy,
security, and integrity, not just on your local computer, but wherever it may ultimately be transmitted
or stored. Identity assurance and access control of electronic transactions and communications is
increasingly required to comply with regulations in finance, law and healthcare applications.