Specifications
Endpoint Encryption for Files and Folders Policy Settings
48 |
didn’t halt. In addition, encrypted files will be scanned later whenever they are
accessed by the user and the encryption keys are there to decrypt the data.
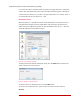
Figure22:ListofKeyRequestExclusions
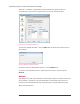
To add a Key Request Exclusion, click the Add button and enter the process name of
the exclusion.
Figure23:AddingaKeyRequestExclusion
To edit the name of a Key Request Exclusion, click the Edit button.
To remove a Key Request Exclusion, select the process name in the list and click
Remove.
Network
This dialog lets you set some parameters controlling encryption on network shares (file
server storage). Changes to any of the parameters in this dialog require the client
machine to be restarted (after having received the policy change) before they take
effect (machine policies).