System information
Comodo Endpoint Security Manager - SME - Administrator Guide
click and drag to swipe the screens left or right) or click a step with a click-able active link below the title bar.
Step 1 - Select Source Type
The new policies can be created from three types of sources:
• Computers - Imports the security settings configured locally from a selected source computer to create a new policy.
• Another Policy - Enables to choose an existing policy and use it as the starting point to create a new policy.
• A saved Policy XML file - Imports the policy from the policy xml file from the computer running the administration
console.
Explanations on importing from different source types can be found in the following sections: Importing from Computers,
Importing from Another Policy and Importing from XML File.
• Select the source type and click the right arrow to move to step 2
Tip: You might create a policy from another policy if you want to exclude a CIS component from policy but use the settings in
other components, or change the agent-specific settings of the policy(such as to have a different compliance polling interval, or
to disallow local mode access) for a particular endpoint or group.
Importing from Computers
• Choose 'A Computer' if you wish to import the security settings from a target endpoint as the new policy and click the
right arrow to move to Step 2 - Selecting Source Computer
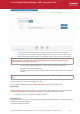
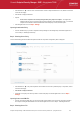
Step 2 - Selecting Source Computer
All endpoint computers added to ESM will be displayed.
• Select the category or group from the left hand side pane. The member endpoints of the selected category/group will
be listed in the right hand side pane.
• Select the computer from which you wish to import the settings. The computer should have CIS installed and be in
local mode, configured as per requirements, and should be online to enable ESM to import the settings.
• Click the filter icon in the 'status' column header to search for a particular endpoint, select the status and click
'Apply'.
Endpoint Security Manager - SME Administrator Guide | © 2013 Comodo Security Solutions Inc. | All rights reserved 128