System information
Comodo Endpoint Security Manager - SME - Administrator Guide
to select all the computers, select the check box beside the 'target computer'. Swipe left (or click the right arrow
button) to move onto the next step.
7. Credentials. Next up is to choose whether the agent has to be installed under the currently logged in user account or
the network administrator account. If you choose 'Custom Credentials', enter the user name and password of an
account with administrative privileges on the machine - such as Administrator, machinename\administrator,
domain\administrator as the login ID. Swipe left (or click the right arrow button) to move onto the next step.
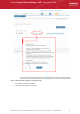
8. The next stage 'Packages' displays the version details of ESM Agent and CIS. You can also check for updates of these
applications and download it in your server for deployment on to the end-points.
9. The final step prior to deployment is to decide whether you also want to install Comodo Internet Security (CIS) at this
time.
• If you want to continue with this process and install CIS now then make sure 'Install Comodo Internet
Security' is enabled and:
(1) Click 'Check for updates' then If any newer versions are available, you can choose to download them to
the ESM server by clicking 'download'.
(2) Choose the CIS version you wish to install from the drop down (most recent is recommended in virtually
all cases).
(3) Choose components to install - Firewall, Antivirus or All Components.
(4) Check 'Suppress Reboot' if you do not want the target endpoint to automatically restart after installation.
Reboot is required to complete installation, but you may want to postpone this until later.
(5) 'Uninstall all incompatible third-party products' - Check this option to uninstall select third party antivirus,
firewall and other desktop security software from the endpoints, prior to the installation of CIS. Performing
this step will remove potentially incompatible products and thus enable CIS to operate correctly. Some
incompatible products can be detected, but not automatically uninstalled and must be removed manually. If
your product is detected but not uninstalled, please consult your vendor’s documentation for precise
uninstallation guidelines.
Click Here to see the full list of incompatible products.
• To move onto the deployment stage, click 'start deployment'. You will see installation progress per-endpoint.
Once installation is complete, you should see a results screen similar to the following screenshot.
Endpoint Security Manager - SME Administrator Guide | © 2013 Comodo Security Solutions Inc. | All rights reserved 21