System information
Comodo Endpoint Security Manager - SME - Administrator Guide
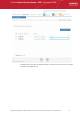
3. Tiles on the dashboard display real-time information regarding connectivity, virus outbreaks and security policy
compliance. Other tiles allow you to quickly launch common tasks such as updating virus databases and running anti-
virus scans. In this first instance, click the 'Total Online' and 'Non-reporting' tiles to check that the import process went
according to plan.
• After checking that all computers are reporting correctly, it is a good idea to make sure the latest virus
databases are installed. Click the 'Outdated' tile to begin this process.
• After updating, we advise running a virus scan on all computers. Click the 'Antivirus Scan' tile to do this.
Note - real-time AV protection is already running on all endpoints. If any malware is discovered, it will be
brought to your attention via the 'Malware Found' tile.
• A full description of the dashboard interface. The meaning of each tile and how to add more tiles can be
found in The Dashboard Area.
• General advice regarding navigation and other functional areas can be found in The Administrative
Console.
Step 5 - Create Groups of computers
In ESM, security policies are applied to 'groups' of computers rather than individual endpoints. Once a group has been created,
admins can run tasks on entire groups of computers (such as applying policy, running AV scans, deploying agents, updating AV
databases and more). 'Policies' are the security configuration of CIS and are imported from specific, already configured,
endpoints then applied to groups (we will cover this in step 6).
• By default, all newly imported computers are placed into a group named 'Unassigned' and inherit that group's security
policy of 'Locally Configured'. Effectively, this means remote management is not in operation and the endpoints will
continue to use the security policy that is already in effect on the endpoint. If needed, the administrator can assign a
policy to 'Unassigned' group so that the policy will be applied to any imported computer and remote management is
enabled immediately.
• We advise admins to create groups corresponding to the structure of their organization THEN import policy (from an
endpoint) and apply it to selected groups. Policies can also later be changed for individual computers in a group,
overriding group policy defaults.
Endpoint Security Manager - SME Administrator Guide | © 2013 Comodo Security Solutions Inc. | All rights reserved 24