Installation guide
Switch Security
6-10
3. The Unapproved APs (Reported by MUs) table displays the following information:
4. The Number of Unapproved APs is simply the sum of all of Unapproved Radio MAC Addresses
detected.
5. Click the Export button to export the contents of the table to a Comma Separated Values file (CSV).
6.3 MU Intrusion Detection
Unauthorized attempts to access the switch managed LAN by MUs is a significant threat to the network, and
one that is very pervasive currently. The switch has several means to protect against threats from MUs trying
to find network vulnerabilities.
Use the switch’s Mobile Unit Intrusion Detection facility to view and configure MU intrusion related
information. The Mobile Unit Intrusion Detection screen provides the following functionalities:
• Configuring MU Intrusion Detection
• Viewing Filtered MUs
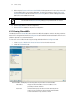
6.3.1 Configuring MU Intrusion Detection
To configure MU intrusion detection:
1. Select Security > Mobile Unit Intrusion Detection from the main tree menu.
BSS MAC Address Displays the MAC Address of each Unapproved AP. These MAC
addresses are access points observed on the network (by
associated MUs), but have yet to be added to the list of approved
APs, and are therefore interpreted as a threat on the network.
Reporting MU Displays the numerical value for the detecting MU.
Last Seen (In Seconds) Displays the time (in seconds) the Unapproved AP was last seen on
the network by the detecting MU.
ESSID Displays the ESSID of each Unapproved AP. These ESSIDs are
device ESSIDs observed on the network, but have yet to be added
to the list of Approved APs and are therefore interpreted as a
threat.