Quick Reference Guide
Table Of Contents
- ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN FVS336Gv2
- Table of Contents
- Introduction
- Connecting the VPN Firewall to the Internet
- Understanding the Connection Steps
- Logging into the VPN Firewall
- Navigating the Menus
- Configuring the Internet Connections
- Automatically Detecting and Connecting
- Manually Configuring the Internet Connection
- Configuring the WAN Mode (Required for Dual WAN)
- Network Address Translation
- Classical Routing
- Configuring Auto-Rollover Mode
- Configuring Load Balancing
- Configuring Dynamic DNS (Optional)
- Configuring the Advanced WAN Options (Optional)
- Additional WAN Related Configuration
- LAN Configuration
- Choosing the VPN Firewall DHCP Options
- Configuring the LAN Setup Options
- Managing Groups and Hosts (LAN Groups)
- Viewing the LAN Groups Database
- Adding Devices to the LAN Groups Database
- Changing Group Names in the LAN Groups Database
- Configuring DHCP Address Reservation
- Configuring Multi Home LAN IP Addresses
- Configuring Static Routes
- Configuring Routing Information Protocol (RIP)
- Firewall Protection and Content Filtering
- About Firewall Protection and Content Filtering
- Using Rules to Block or Allow Specific Kinds of Traffic
- About Services-Based Rules
- Viewing the Rules
- Order of Precedence for Rules
- Setting the Default Outbound Policy
- Creating a LAN WAN Outbound Services Rule
- Creating a LAN WAN Inbound Services Rule
- Modifying Rules
- Inbound Rules Examples
- Outbound Rules Example
- Configuring Other Firewall Features
- Attack Checks
- Configuring Session Limits
- Managing the Application Level Gateway for SIP Sessions
- Creating Services, QoS Profiles, and Bandwidth Profiles
- Adding Customized Services
- Setting Quality of Service (QoS) Priorities
- Creating Bandwidth Profiles
- Setting a Schedule to Block or Allow Specific Traffic
- Blocking Internet Sites (Content Filtering)
- Configuring Source MAC Filtering
- Configuring IP/MAC Address Binding
- Configuring Port Triggering
- E-Mail Notifications of Event Logs and Alerts
- Administrator Tips
- Virtual Private Networking Using IPsec
- Considerations for Dual WAN Port Systems
- Using the VPN Wizard for Client and Gateway Configurations
- Creating Gateway to Gateway VPN Tunnels with the Wizard
- Creating a Client to Gateway VPN Tunnel
- Testing the Connections and Viewing Status Information
- NETGEAR VPN Client Status and Log Information
- VPN Firewall VPN Connection Status and Logs
- Managing VPN Policies
- Configuring IKE Policies
- Configuring VPN Policies
- Configuring Extended Authentication (XAUTH)
- Configuring XAUTH for VPN Clients
- User Database Configuration
- RADIUS Client Configuration
- Assigning IP Addresses to Remote Users (ModeConfig)
- Mode Config Operation
- Configuring Mode Config Operation on the VPN Firewall
- Configuring the ProSafe VPN Client for ModeConfig
- Configuring Keepalives and Dead Peer Detection
- Configuring Keepalives
- Configuring Dead Peer Detection
- Configuring NetBIOS Bridging with VPN
- Virtual Private Networking Using SSL
- Understanding the Portal Options
- Planning for SSL VPN
- Creating the Portal Layout
- Configuring Domains, Groups, and Users
- Configuring Applications for Port Forwarding
- Adding Servers
- Adding A New Host Name
- Configuring the SSL VPN Client
- Configuring the Client IP Address Range
- Adding Routes for VPN Tunnel Clients
- Replacing and Deleting Client Routes
- Using Network Resource Objects to Simplify Policies
- Adding New Network Resources
- Configuring User, Group, and Global Policies
- Viewing SSL VPN Policies
- Adding an SSL VPN Policy
- Managing Users, Authentication, and Certificates
- Adding Authentication Domains, Groups, and Users
- Creating a Domain
- Creating a Group
- Creating a New User Account
- Setting User Login Policies
- Changing Passwords and Other User Settings
- Managing Certificates
- Viewing and Loading CA Certificates
- Viewing Active Self Certificates
- Obtaining a Self Certificate from a Certificate Authority
- Managing your Certificate Revocation List (CRL)
- VPN Firewall and Network Management
- Performance Management
- Bandwidth Capacity
- Features That Reduce Traffic
- Features That Increase Traffic
- Using QoS to Shift the Traffic Mix
- Tools for Traffic Management
- Changing Passwords and Administrator Settings
- Enabling Remote Management Access
- Using the Command Line Interface
- Using an SNMP Manager
- Managing the Configuration File
- Reverting to Factory Default Settings
- Configuring Date and Time Service
- Monitoring System Performance
- Enabling the Traffic Meter
- Activating Notification of Events and Alerts
- Viewing the Logs
- Viewing VPN Firewall Configuration and System Status
- Monitoring VPN Firewall Statistics
- Monitoring the Status of WAN Ports
- Monitoring Attached Devices
- Viewing the DHCP Log
- Monitoring Active Users
- Viewing Port Triggering Status
- Monitoring VPN Tunnel Connection Status
- Viewing the VPN Logs
- Troubleshooting
- Basic Functions
- Power LED Not On
- LEDs Never Turn Off
- LAN or WAN Port LEDs Not On
- Troubleshooting the Web Configuration Interface
- Troubleshooting the ISP Connection
- Troubleshooting a TCP/IP Network Using a Ping Utility
- Testing the LAN Path to Your VPN Firewall
- Testing the Path from Your PC to a Remote Device
- Restoring the Default Configuration and Password
- Problems with Date and Time
- Using the Diagnostics Utilities
- Default Settings and Technical Specifications
- Network Planning for Dual WAN Ports
- What You Need to Do Before You Begin
- Cabling and Computer Hardware Requirements
- Computer Network Configuration Requirements
- Internet Configuration Requirements
- Where Do I Get the Internet Configuration Parameters?
- Internet Connection Information Form
- Overview of the Planning Process
- Inbound Traffic
- Virtual Private Networks (VPNs)
- The Roll-over Case for Firewalls With Dual WAN Ports
- The Load Balancing Case for Firewalls with Dual WAN Ports
- Inbound Traffic
- Inbound Traffic to Single WAN Port (Reference Case)
- Inbound Traffic to Dual WAN Port Systems
- Virtual Private Networks (VPNs)
- VPN Road Warrior (Client-to-Gateway)
- VPN Gateway-to-Gateway
- VPN Telecommuter (Client-to-Gateway Through a NAT Router)
- Two Factor Authentication
- Related Documents
- Notification of Compliance
- Index
68 | Chapter 4: Firewall Protection and Content Filtering
ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN FVS336Gv2 Reference Manual
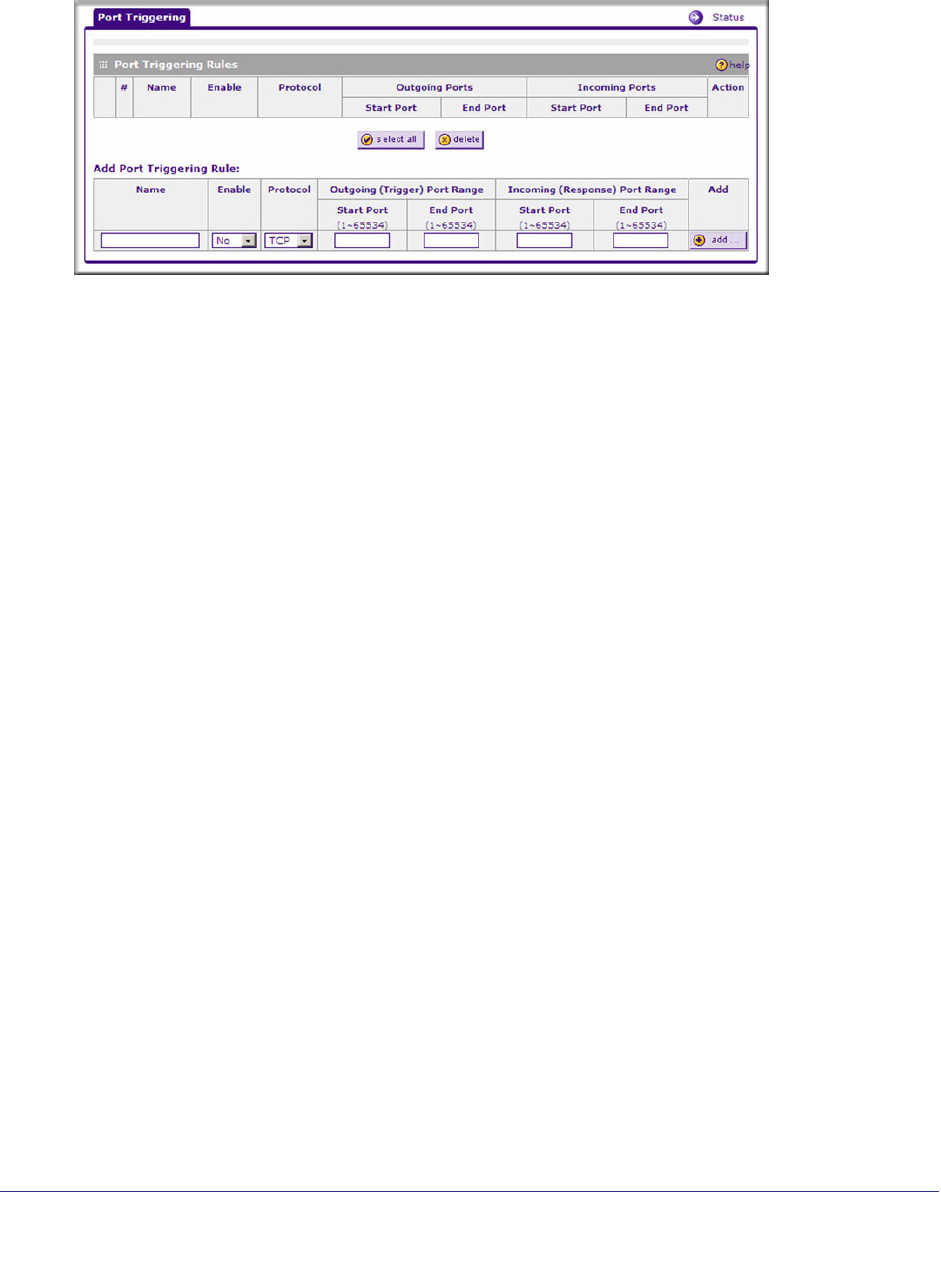
To add a port triggering rule:
1. Select Security > Port Triggering to display the Port Triggering screen.
2. Enter a user-defined name for this rule in the Name field.
3. In the Enable field, indicate if the rule is enabled or disabled.
4. in the Protocol field, choose either TCP or UDP transport protocol.
5. In the Outgoing (Trigger) Port Range fields:
a. Enter the Start Port range (1 - 65534).
b. Enter the End Port range (1 - 65534).
6. In the Incoming (Response) Port Range fields:
a. Enter the Start Port range (1 - 65534).
b. Enter the End Port range (1 - 65534).
7. Click Add. The port triggering rule will be added to the Port Triggering Rules table.
To check the status of the port triggering rules, click the Status option arrow to the right of the
tab on the Port Triggering screen. The following data is displayed:
• Rule – The name of the port triggering rule.
• LAN IP Address – The IP address of the PC currently using this rule.
• Open Ports – The incoming ports associated with this rule. Incoming traffic using these
ports will be sent to the LAN IP address above.
• Time Remaining – The time remaining before this rule is released, and thus available for
other PCs. The timer is reset whenever incoming or outgoing traffic is received.
E-Mail Notifications of Event Logs and Alerts
The firewall logs can be configured to log and then e-mail denial of access, general attack
information, and other information to a specified e-mail address. For example, your VPN
firewall will log security-related events such as: accepted and dropped packets on different
segments of your LAN; denied incoming and outgoing service requests; hacker probes and
login attempts; and other general information based on the settings that you enter on the










