User Manual
Table Of Contents
- Chapter 1. Product Introduction
- Chapter 2. Hardware Installation
- Chapter 3. Connecting to the AP
- Chapter 4. Quick Installation Guide
- Chapter 5. Configuring the AP
- 5.1 Status
- 5.2 Quick Setup
- 5.3 WPS
- 5.4 Operation Mode
- 5.5 Network
- 5.6 Wireless
- 5.6.1 Wireless Settings
- 5.6.2 Wireless Security
- 5.6.2.1. Operation Mode – Access Point
- 5.6.2.2. Operation Mode – Multi-SSID
- 5.6.2.3. Operation Mode – Client
- 5.6.2.4. Operation Mode – Repeater
- 5.6.2.5. Operation Mode – Universal Repeater
- 5.6.2.6. Operation Mode – Bridge with AP
- 5.6.2.7. Operation Mode – AP Router
- 5.6.2.8. Operation Mode – AP Client Router
- 5.6.3 Wireless MAC Filtering
- 5.6.4 Wireless Advanced
- 5.6.5 Antenna Alignment
- 5.6.6 Distance Setting
- 5.6.7 Throughput Monitor
- 5.6.8 Wireless Statistics
- 5.7 DHCP
- 5.8 Forwarding
- 5.9 Security
- 5.10 Parental Control
- 5.11 Access Control
- 5.12 Static Routing
- 5.13 Bandwidth Control
- 5.14 IP & MAC Binding
- 5.15 Dynamic DNS
- 5.16 System Tools
- Appendix A: FAQ
- A.1 What and how to find my PC’s IP and MAC address?
- A.2 What is Wireless LAN?
- A.3 What are ISM bands?
- A.4 How does wireless networking work?
- A.5 What is BSSID?
- A.6 What is ESSID?
- A.7 What are potential factors that may causes interference?
- A.8 What are the Open System and Shared Key authentications?
- A.9 What is WEP?
- A.10 What is Fragment Threshold?
- A.11 What is RTS (Request to Send) Threshold?
- A.12 What is Beacon Interval?
- A.13 What is Preamble Type?
- A.14 What is SSID Broadcast?
- A.15 What is Wi-Fi Protected Access (WPA)?
- A.16 What is WPA2?
- A.17 What is 802.1x Authentication?
- A.18 What is Temporal Key Integrity Protocol (TKIP)?
- A.19 What is Advanced Encryption Standard (AES)?
- A.20 What is Inter-Access Point Protocol (IAPP)?
- A.21 What is Wireless Distribution System (WDS)?
- A.22 What is Universal Plug and Play (UPnP)?
- A.23 What is Maximum Transmission Unit (MTU) Size?
- A.24 What is Clone MAC Address?
- A.25 What is DDNS?
- A.26 What is NTP Client?
- A.27 What is VPN?
- A.28 What is IPSEC?
- A.29 What is WLAN Block Relay between Clients?
- A.30 What is WMM?
- A.31 What is WLAN ACK TIMEOUT?
- A.32 What is Modulation Coding Scheme (MCS)?
- A.33 What is Frame Aggregation?
- A.34 What is Guard Intervals (GI)?
- Appendix B: Configuring the PC in Windows 7
- Appendix C: Specifications
- Appendix D: Factory Default Settings
- EC Declaration of Conformity
User Manual of WNAP-7206
-107-
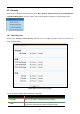
Incoming Port
The port or port range used by the remote system when it responds
to the outgoing request. A response using one of these ports will be
forwarded to the PC which triggered this rule. You can input at
most 5 groups of ports (or port sections). Every group of ports must
be separated with ",". For example, 2000-2038, 2046, 2050-2051,
2085, 3010-3030.
Incoming Protocol
The protocol used for Incoming Port, either TCP, UDP, or ALL (all
protocols are supported by the Device.).
Status
The status of this entry. Enabled means the Port Triggering entry is
enabled.
Modify
To modify or delete an existing entry.
Common
Applications
Some popular applications already listed in the from the pull-down
list of Incoming Protocol.
There are many popular applications in the Common Application list. You can select an application and then
the boxes of Trigger Port and Incoming Ports will be automatically filled in. This has the same effect as
adding a new rule.
To modify or delete an existing entry:
1. Find the desired entry in the table.
2. Click Modify or Delete as desired on the Modify column.
Click the Enable All button to enable all entries.
Click the Disable All button to disable all entries.
Click the Delete All button to delete all entries.
Click the Next button to go to the next page and Click the Previous button to return to the previous
page.
1. When the trigger connection is released, the corresponding opened ports will
be closed.
2. Each rule can only be used by one host on the LAN at a time. The trigger
connection of other hosts on the LAN will be refused.
3. Incoming Ports ranges cannot overlap each other.