Owner's manual
Table Of Contents
- Chapter 1: Introduction
- Chapter 2: Accessing CC-SG
- Chapter 3: Configuring CC-SG with Guided Setup
- Chapter 4: Creating Associations
- Chapter 5: Adding Devices and Device Groups
- Chapter 6: Configuring Nodes and Interfaces
- Chapter 7: Adding and Managing Users and User Groups
- Chapter 8: Policies
- Chapter 9: Configuring Remote Authentication
- Chapter 10: Generating Reports
- Audit Trail Report
- Error Log Report
- Access Report
- Availability Report
- Active Users Report
- Locked Out Users Report
- User Data Report
- Users in Groups Report
- Group Data Report
- AD User Group Report
- Asset Management Report
- Node Asset Report
- Active Nodes Report
- Node Creation Report
- Query Port Report
- Active Ports Report
- Scheduled Reports
- CC-NOC Synchronization Report
- Chapter 11: System Maintenance
- Chapter 12: Advanced Administration
- Appendix A: Specifications (G1, V1, and E1)
- Appendix B: CC-SG and Network Configuration
- Appendix C: User Group Privileges
- Appendix D: SNMP Traps
- Appendix E: Troubleshooting
- Appendix F: Two-Factor Authentication
- Appendix G: FAQs
- Appendix H: Keyboard Shortcuts
APPENDIX B: CC-SG AND NETWORK CONFIGURATION 219
The first mode is the primary means for users and administrators to connect to CC-SG. The other
two modes are less frequently used. These modes require the following networking configuration:
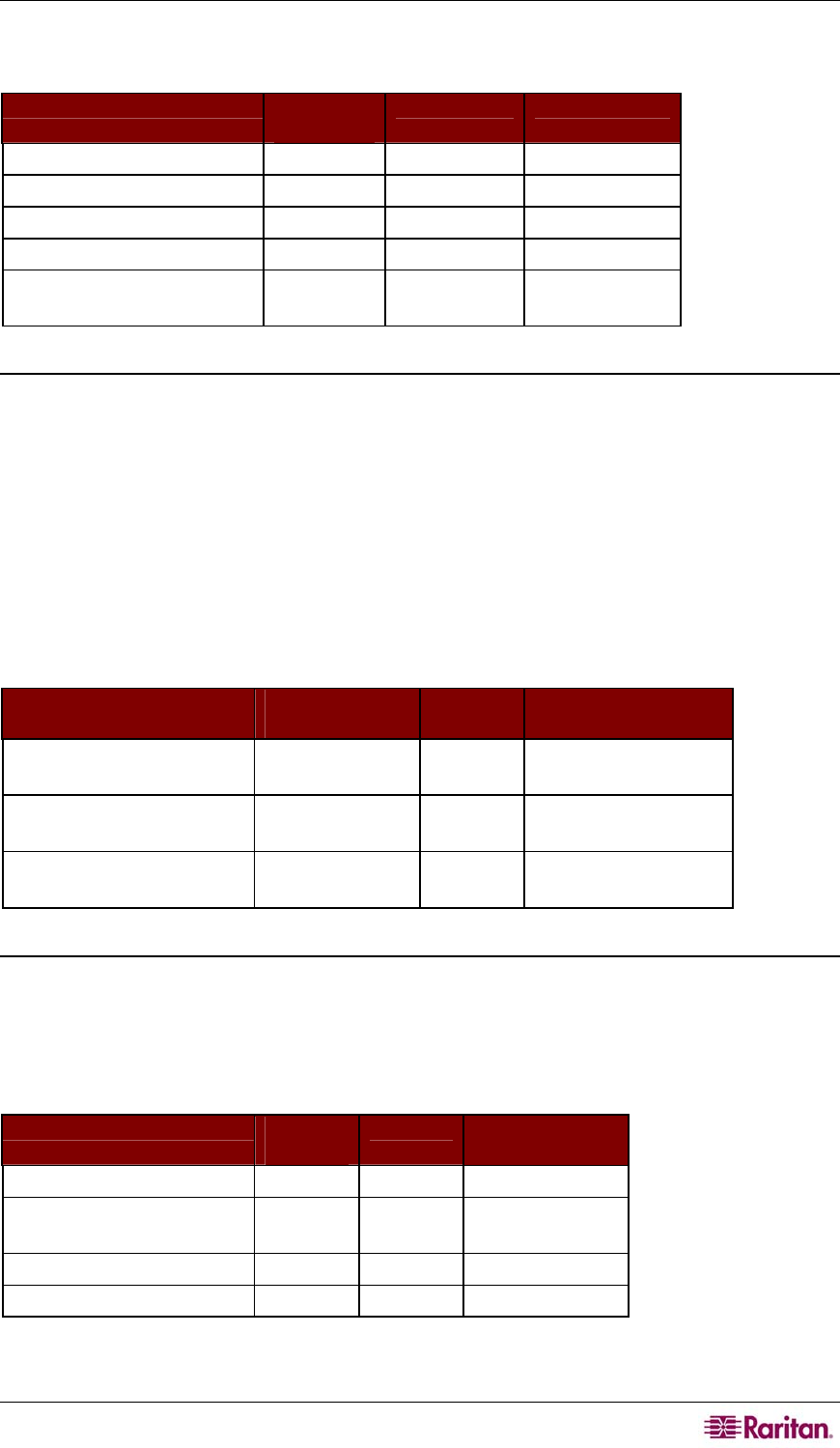
Communication Direction Port
Number
Protocol Configurable?
Client → CC-SG GUI 443 TCP no
Client → CC-SG GUI 80 TCP no
Client → CC-SG GUI 8080 TCP no
Client → CC-CLI SSH 22 TCP yes
Client → CC Diagnostic
Console
23 TCP yes
PC Clients to Nodes
Another significant role of CC-SG is to connect PC clients to various targets (or nodes). These
targets can be serial or KVM console connections to Raritan devices (called Out-of-Band
connections). Another mode is to use In-Band access (IBA) methods, for example, Virtual
Network Computer (VNC), Windows Remote Desktop (RDP), or Secure Shell (SSH).
Another facet of PC client to target communication is whether:
• The PC client connects directly to the target (either via a Raritan device or In-Band access),
which is called Direct Mode.
• Or, if the PC client connects to the target through CC-SG, which acts as an application
firewall and is called Proxy Mode.
Communication Direction Port
Number
Protocol Configurable?
Client → CC-SG via Proxy
→ Target
2400
(on CC-SG)
TCP no
Client → Raritan Target
(Direct Mode)
5000 (on device) TCP yes
Client → Dominion SX →
(Direct Mode)
51000 TCP yes
CC-SG & Client for IPMI, iLO/RILOE, DRAC, RSA
Another significant role of CC-SG is to manage third-party devices, such as iLO/RILOE, Hewlett
Packard’s Integrated Lights Out/Remote Insight Lights Out servers. Targets of an iLO/RILOE
device are powered on/off and recycled directly. Intelligent Platform Management Interface
(IPMI) servers can also be controlled by CC-SG. Dell DRAC and RSA targets can also be
managed by CC-SG.
Communication Direction Port
Number
Protocol Configurable
CC-SG → IPMI 623 UDP no
CC-SG → iLO/RILOE (uses
HTTP ports)
80 or 443 UDP no
CC-SG → DRAC 80 or 443 UDP no
CC-SG → RSA 80 or 443 UDP no










