User Manual
Multi-Function Gigabit Wireless-N Client Bridge
Version 1.0
26
This option works with a RADIUS Server to authenticate wireless clients. Wireless clients
should have established the necessary credentials before attempting to authenticate to the
Server through this Gateway. Furthermore, it may be necessary to configure the RADIUS
Server to allow this Gateway to authenticate users.
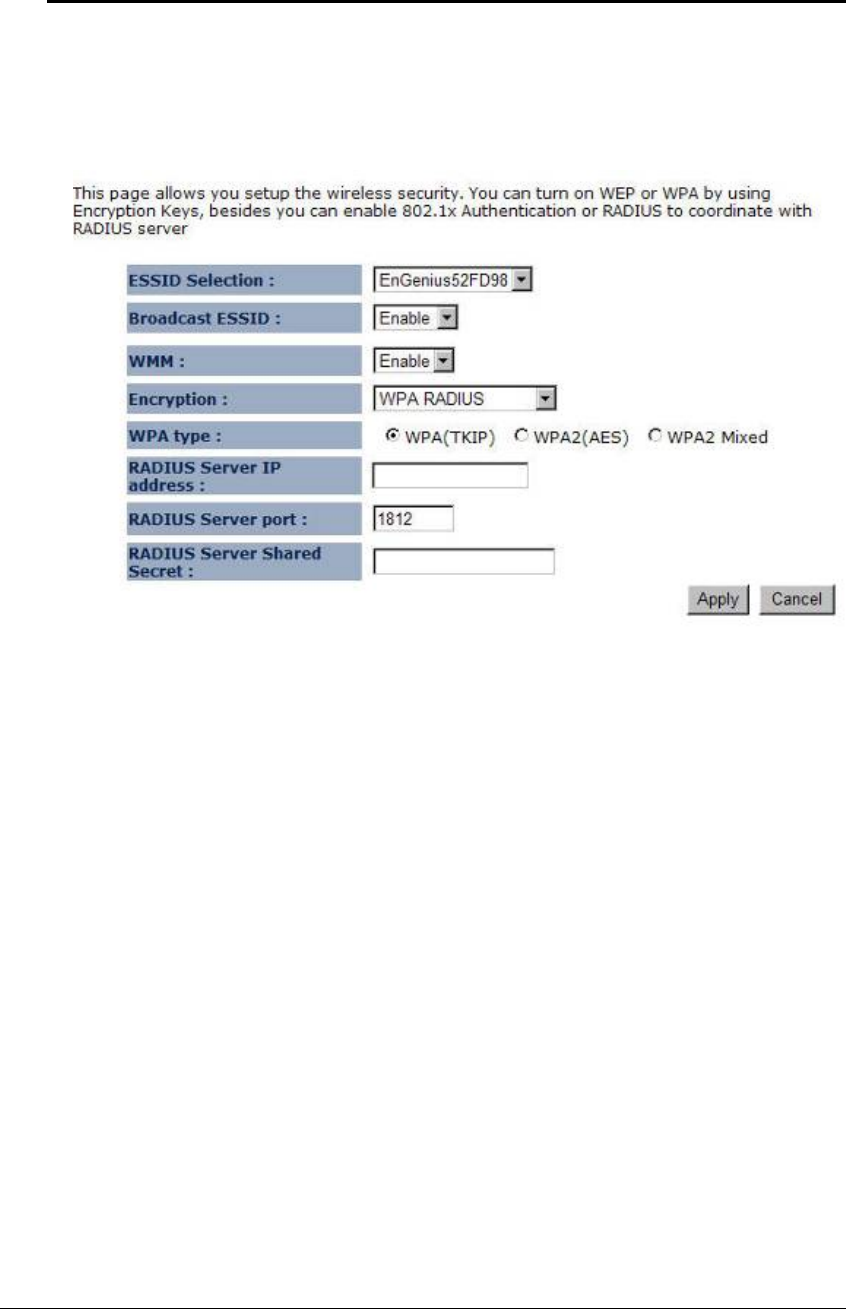
ESSID Selection: As this device supports multiple SSIDs, it is possible to configure a
different security mode for each SSID (profile). Select an SSID from the drop-down list.
Broadcast SSID: Select Enable or Disable from the drop-down list. This is the SSID
broadcast feature.
When this option is set to Enable, your wireless network name is broadcast to
anyone within the range of your signal
. If you're not using encryption then they could connect to
your network. When this is disabled, you must enter the Wireless Network Name (SSID) on
the client manually to connect to the network.
WMM: Choose to Enable or Disable WMM. This is the Quality of Service (QoS) feature for
prioritizing voice and video applications. This option can be further configured in WMM
under the Wireless drop-down menu.
Encryption: Select WPA RADIUS from the drop-down list.
WPA Type: Select TKIP, AES, or WPA2 Mixed. The encryption algorithm used to secure
the data communication. TKIP (Temporal Key Integrity Protocol) provides per-packet key
generation and is based on WEP. AES (Advanced Encryption Standard) is a very secure
block based encryption. Note that, if the bridge uses the AES option, the bridge can associate
with the access point only if the access point is also set to use only AES.
RADIUS Server IP Address: Specify the IP address of the RADIUS server.
RADIUS Server Port: Specify the port number of the RADIUS server, the default port is
1812.
RADIUS Server Password: Specify the pass-phrase that is matched on the RADIUS Server.
Click on the Apply button to save the changes.
3.2.4.2.5 Filter
You will be able to block out connections from unauthorized MAC Address by setting filter
policy.










