User's Manual Part 4
Access / One
®
Network
Managing Modules 165
7
The Rogue Devices Function
This function provides you with a rogue scanning tool that allows you to scan for all
rogue devices. The scanning tool offered here is similar to the Rogue Monitor tool
provided at the network level, but applies only to rogue devices detected by the
wireless module that you are logged in to.
Commands
This area of Manger/One applies to wireless modules only.
Scan
Use this command if you want to initiate an active scan for rogue devices. Active
scans can take up to one minute to complete and traffic to and from the module will
be disrupted during the scanning process. Results from the scan are reported in the
Rogue Monitor table.
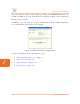
Figure 127. Rogue Monitor Table
The table displayed in the Rogue Monitor table can be sorted in either ascending or
descending order based on any selected column. For example, if you want to sort
the table by technology, click in the column header for Technology—the table is
then sorted according to the wireless technology used by the rogue device. The
default is to have the table sorted by BSSID in descending order.