Operation Manual
© Copyright 2013 TRENDnet. All Rights Reserved.
TRENDnet User’s Guide
TEW-752DRU
31
Create schedules
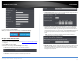
Tools > Schedules
For additional security control, your router allows you to create schedules to specify a
time period when a feature on your router should be activated and deactivated. Before
you use the scheduling feature on your router, ensure that your router system time is
configured correctly.
Note: You can apply a predefined schedule to the following features:
• Wireless (2.4GHz and 5GHz)
• Wireless Guest Zone
• MAC Filters
• Virtual Server
• Firewall Rules
• Application Rules
• Parental Control (Website Filtering)
1. Log into your router management page (see “Access your router management page
”
on page 25).
2. Click on Tools and click on Schedules.
3. Review the Schedule settings. Click Save Settings to save settings.
• Name: Enter a name for the schedule you would like to apply.
• Day(s)/Select Day(s): Check Select Day(s) to select the days in the Select Day(s)
section or select All Week to set the schedule for all days.
• All Day – 24 Hours: Check the option to set the schedule to 24 hours or define
the schedule under Start Time and End Time.
• Start/End Time: Select the start and end time you would like the schedule to
follow.
Note: The schedule defined will define the time/day the feature will be activated.
Open a device on your network to the Internet
This router can provide access to devices on your local area network to the Internet
using the Virtual Server, Special Application, method (DMZ NOT recommended).
DMZ
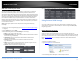
Access > Firewall & DMZ
You may want to expose a specific computer or device on your network to the Internet
to allow anyone to access it. Your router includes the DMZ (Demilitarized Zone) feature
that makes all the ports and services available on the WAN/Internet side of the router
and forwards them to a single IP address (computer or network device) on your
network. The DMZ feature is an easy way of allowing access from the Internet however,
it is a very insecure technology and will open local area network to greater threats from
Internet attacks.
It is strongly recommended to use Virtual Server (also called port forwarding, see
“Virtual Server
” on page 35) to allow access to your computers or network devices from
the Internet.
1. Make the computer or network device (for which you are establishing a DMZ link) has
a static IP address. Signing up for a Dynamic DNS service (outlined in
Identify Your