User`s guide
Technical white paper
34
Rules
Rules are used to trigger an Action when a specific event or event(s) occur. Keeping with our Failed Logon example we are
going to create a Rule named Failed Logon Notify that will trigger an email when three failed logons occur on the same host
within two minutes.
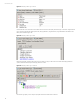
The Rules configuration is similar to the Query configuration. Use the Rule Editor to define the Conditions. We are going to
use the same condition that was specified in out Failed Logon Query to identify failed logon events by specifying the
Category Behavior equal to /Authentication/Verify and Category Outcome = /Failure as shown in Figure 42.
Figure 42. HP ArcSight ESM Rule Editor – Conditions
Next we’ll configure the Aggregation tab, in this section we configure the rule to execute after a defined number of events
occur within a specified time period on a single host, three times in two minutes, on the same Target Host Name. The fields
of the events can be matched if they are the same or unique. In this example we have selected the Target Host Name field
to be the same for three events during a two minute span. Other event fields could be added, for example Attacker User
Name or Attacker Address. Once configured the Rule Aggregation Summary will display the following:
• Aggregate if at least 3 matching conditions are found within 2 Minutes AND these event fields are the same
(event1.Target Zone Resource, event1.Target Host Name)
The Actions tab specifies the action to take when the conditions of a Rule are met. We can configure actions to occur as
specified in the Actions tab. We have chosen to trigger the Send Notification action On Every Event. Selecting Send
Notification will prompt you to specify a destination and a brief message for the email body.
Figure 43. HP ArcSight ESM Rule Editor – Actions Summary
In our example we have chosen to send a message to the SOC Operators group and with a message Failed Logons occurred.