User guide
Table Of Contents
- Part1
- Part2
- Part2
- Part3
- Part4
- Part5
- Dynamic Link Aggregation
- Link Aggregation ID
- RADIUS
- Configuring RADIUS Server Settings
- Configuring IEEE802.1x
- Supported MIBs
- SNMP Traps
- Configuring SNMP
- Setting Up Login Accounts
- Requirements for Using SSH
- HTTPS Example
- Internet Explorer Warning Messages
- Netscape Navigator Warning Messages
- Login Screen
- Strict Priority Queuing (SPQ)
- Weighted Round Robin Scheduling (WRR)
- DiffServ
- DSCP and Per-Hop Behavior
- DHCP “Relay Agent Information Option”
- DHCP Relay Agent Circuit ID Sub-option Format
- Part6
- Part7
- Switch Configuration File
- Access Priority
- The Console Port
- Telnet
- List of Available Commands
- Detailed Command Information
- Logging Out
- User Mode
- Enable Mode
- Configure Mode
- config-vlan Commands
- interface Commands
- show system-information
- show hardware-monitor
- show ip
- show logging
- show interface
- show mac address-table
- Backing up Configuration
- Restoring Configuration
- Using a Different Configuration File
- Resetting to the Factory Default
- no mirror-port
- no https timeout
- no trunk
- no port-access-authenticator
- no ssh
- interface
- bpdu-control
- broadcast-limit
- bandwidth-limit
- mirror
- gvrp
- ingress-check
- frame-type
- vlan-trunking
- spq
- wrr
- egress set
- qos priority
- name
- speed-duplex
- Static Entries (SVLAN Table)
- Dynamic Entries (DVLAN Table)
- GARP Status
- GARP Timer
- GVRP Timer
- Enable GVRP
- Disable GVRP
- Set Port VID
- Set Acceptable Frame Type
- Enable or Disable Port GVRP
- Modify Static VLAN
- Delete VLAN ID
Dimension GS-3012 Gigabit Ethernet Switch
Access Control 17-7
17.7 Introduction to HTTPS
HTTPS (HyperText Transfer Protocol over Secure Socket Layer, or HTTP over SSL) is a web protocol that
encrypts and decrypts web pages. Secure Socket Layer (SSL) is an application-level protocol that enables secure
transactions of data by ensuring confidentiality (an unauthorized party cannot read the transferred data),
authentication (one party can identify the other party) and data integrity (you know if data has been changed).
It relies upon certificates, public keys, and private keys.
HTTPS on the switch is used so that you may securely access the switch using the web configurator. The SSL
protocol specifies that the SSL server must always authenticate itself to the SSL client (the computer which
requests the HTTPS connection with the switch), whereas the SSL client only should authenticate itself when the
SSL server requires it to do so.
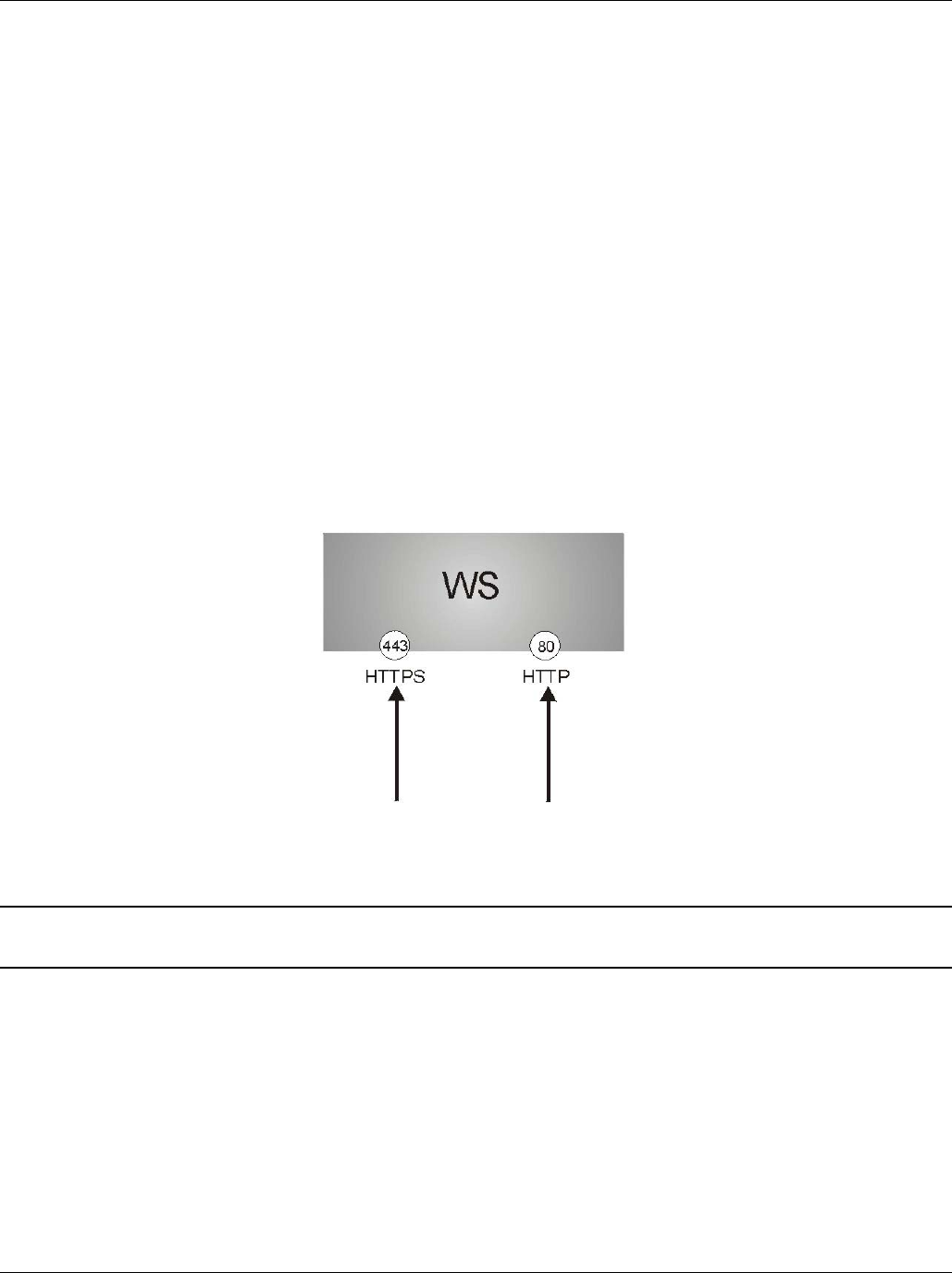
Please refer to the following figure.
Step 1. HTTPS connection requests from an SSL-aware web browser go to port 443 (by default) on the switch’s
WS (web server).
Step 2. HTTP connection requests from a web browser go to port 80 (by default) on the switch’s WS.
Figure 17-8 HTTPS Implementation
If you disable HTTP in the Service Access Control screen, then the switch blocks all HTTP
connection attempts.
17.7.1 HTTPS Example
If you haven’t changed the default HTTPS port on the switch, then in your browser enter “https:// switch IP
Address/” as the web site address where “switch IP Address” is the IP address or domain name of the switch you
wish to access.
The HTTPS proxy server listens on port 443 by default. If you change the HTTPS proxy server port to a different
number on the switch, for example 8443, then you must notify people who need to access the switch web
configurator to use “https:// switch IP Address:8443” as the URL.










