Setup Guide
Table Of Contents
- 1 Introduction
- 2 iDRAC9 Configuration for RSA SecurID
- 3 RSA SecurID 2FA with Local Users
- 4 RSA SecurID 2FA with Active Directory Users
- 5 RSA SecurID 2FA with Generic LDAP Directory Users
- 6 Troubleshooting RSA SecurID Issues
- 6.1 Misconfiguration or iDRAC Configuration Gets Reset
- 6.2 Datacenter License Expires or Gets Downgraded or Deleted
- 6.3 Authentication Failures without being Prompted for RSA Passcode
- 6.4 Authentication failures with Correct RSA Passcode
- 6.5 Authentication Failures with Correct RSA Passcode due to Timeout
- 6.6 RSA Configuration gets lost after importing Server Configuration Profile
- Appendix A: Configure iDRAC Using RACADM
- Appendix B: References
iDRAC9 Configuration for RSA SecurID
ID 450
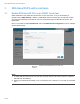
RSA SecurID Configuration Page
Warning: For RSA AM adminsitrators, iDRAC does NOT support RSA Access ID. RSA Access ID can be
used for additional security to ensure the integrity of RSA authentication message exchange. However, make
sure this feature is disabled. Note that “disabled” is the default setting of the RSA AM server.
2.2 RSA AM Server Certificate (chain) Upload
RSA AM server certificate or certificate chain must be uploaded into iDRAC so that iDRAC can securely
communicate with the configured RSA AM server.
In Figure-1, the RSA SecurID Configuration page allows you to upload the RSA server certificate. Contact
your RSA AM server administrator to get the certificate or certificate chain in PEM format. Alternatively, you
may also use RACADM to upload the certificate file into iDRAC. Use the subcommand sslcertupload with type
option set to “RSA CA Certificate.” See RACADM Users Guide for further details.
Alternatively, you may run the following command to retrieve the certificate chain. First, remove openssl
debug information. Maintain the certificates in a file that can be uploaded later into iDRAC.
$ openssl s_client -showcerts -connect <rsa-am-server-hostname>:5555
2.3 Test Connection to RSA AM Server
Before you can test connectivity to the RSA AM server:
• Specify all global settings.